The Basic Strategy of Log File Reading Is to Determine What Traffic Is Usual. True False
What is a firewall?
A firewall is software or firmware that prevents unauthorized admission to a network. It inspects incoming and outgoing traffic using a fix of rules to identify and block threats.
Firewalls are used in both personal and enterprise settings, and many devices come with one built-in, including Mac, Windows, and Linux computers. They are widely considered an essential component of network security.
Why are firewalls important?
Firewalls are important because they accept had a huge influence on mod security techniques and are nonetheless widely used. They showtime emerged in the early days of the net, when networks needed new security methods that could handle increasing complexity. Firewalls have since become the foundation of network security in the client-server model – the central architecture of mod calculating. Most devices use firewalls – or closely related tools – to inspect traffic and mitigate threats.
Uses
Firewalls are used in both corporate and consumer settings. Modern organizations incorporate them into a security information and consequence management (SIEM) strategy along with other cybersecurity devices. They may be installed at an organization's network perimeter to baby-sit against external threats, or within the network to create segmentation and guard confronting insider threats.
In addition to immediate threat defence, firewalls perform important logging and inspect functions. They keep a record of events, which can exist used by administrators to identify patterns and meliorate rule sets. Rules should be updated regularly to keep up with always-evolving cybersecurity threats. Vendors notice new threats and develop patches to cover them as soon as possible.
In a single dwelling house network, a firewall tin can filter traffic and alert the user to intrusions. They are peculiarly useful for ever-on connections, like Digital Subscriber Line (DSL) or cablevision modem, because those connectedness types use static IP addresses. They are often used aslope to antivirus applications. Personal firewalls, unlike corporate ones, are usually a unmarried product as opposed to a drove of various products. They may be software or a device with firewall firmware embedded. Hardware/firmware firewalls are oftentimes used for setting restrictions between in-abode devices.
How does a firewall work?
A firewall establishes a border between an external network and the network it guards. Information technology is inserted inline across a network connectedness and inspects all packets entering and leaving the guarded network. As information technology inspects, it uses a set up of pre-configured rules to distinguish between benign and malicious packets.
The term 'packets' refers to pieces of information that are formatted for net transfer. Packets contain the information itself, as well equally data about the data, such as where it came from. Firewalls can use this packet information to determine whether a given package abides by the rule set. If it does non, the parcel volition be barred from entering the guarded network.
Dominion sets can exist based on several things indicated by packet data, including:
- Their source.
- Their destination.
- Their content.
These characteristics may be represented differently at different levels of the network. As a packet travels through the network, it is reformatted several times to tell the protocol where to transport it. Different types of firewalls be to read packets at different network levels.
Types of firewalls
Firewalls are either categorized by the fashion they filter data, or by the system they protect.
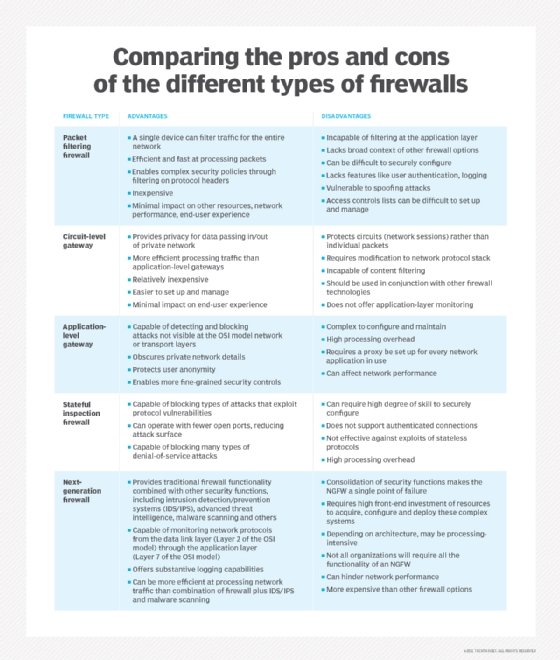
When categorizing past what they protect, the two types are: network-based and host-based. Network-based firewalls guard unabridged networks and are oftentimes hardware. Host-based firewalls guard individual devices – known equally hosts – and are often software.
When categorizing past filtering method, the main types are:
- A bundle-filtering firewall examines packets in isolation and does not know the packet's context.
- A stateful inspection firewall examines network traffic to determine whether i packet is related to another packet.
- A proxy firewall (aka application-level gateway) inspects packets at the application layer of the Open Systems Interconnection (OSI) reference model.
- A Next Generation Firewall (NGFW) uses a multilayered approach to integrate enterprise firewall capabilities with an intrusion prevention system (IPS) and application control.
Each type in the list examines traffic with college level of context than the 1 before – ie, stateful has more than context than parcel-filtering.
Packet-filtering firewalls
When a packet passes through a packet-filtering firewall, its source and destination address, protocol and destination port number are checked. The packet is dropped – meaning not forwarded to its destination – if it does non comply with the firewall's rule ready. For instance, if a firewall is configured with a rule to block Telnet access, then the firewall will drop packets destined for Manual Control Protocol (TCP) port number 23, the port where a Telnet server application would be listening.
A packet-filtering firewall works mainly on the network layer of the OSI reference model, although the transport layer is used to obtain the source and destination port numbers. It examines each packet independently and does not know whether whatever given parcel is part of an existing stream of traffic.
The parcel-filtering firewall is constructive, only because it processes each packet in isolation, it can be vulnerable to IP spoofing attacks and has largely been replaced past stateful inspection firewalls.
Stateful inspection firewalls
Stateful inspection firewalls – as well known as dynamic packet-filtering firewalls – monitor advice packets over time and examine both incoming and outgoing packets.
This type maintains a table that keeps track of all open connections. When new packets arrive, it compares data in the packet header to the land table – its list of valid connections – and determines whether the packet is part of an established connection. If information technology is, the parcel is let through without further assay. If the package does not match an existing connection, it is evaluated co-ordinate to the rule gear up for new connections.
Although stateful inspection firewalls are quite constructive, they can be vulnerable to denial-of-service (DoS) attacks. DoS attacks work by taking advantage of established connections that this type generally assumes are condom.
Application layer and proxy firewalls
This type may also be referred to every bit a proxy-based or reverse-proxy firewall. They provide application layer filtering and can examine the payload of a packet to distinguish valid requests from malicious code bearded as a valid request for data. As attacks against spider web servers became more common, it became apparent that there was a need for firewalls to protect networks from attacks at the application layer. Packet-filtering and stateful inspection firewalls cannot practice this at the awarding layer.
Since this type examines the payload'south content, information technology gives security engineers more granular control over network traffic. For example, it can allow or deny a specific incoming Telnet control from a particular user, whereas other types can only command general incoming requests from a particular host.
When this blazon lives on a proxy server – making it a proxy firewall -- it makes information technology harder for an assaulter to discover where the network actually is and creates yet another layer of security. Both the client and the server are forced to behave the session through an intermediary -- the proxy server that hosts an application layer firewall. Each fourth dimension an external customer requests a connexion to an internal server or vice versa, the client will open a connexion with the proxy instead. If the connection asking meets the criteria in the firewall rule base, the proxy firewall volition open up a connexion to the requested server.
The key do good of awarding layer filtering is the power to block specific content, such as known malware or certain websites, and recognize when certain applications and protocols, such as Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP) and domain name system (DNS), are beingness misused. Application layer firewall rules tin also be used to control the execution of files or the handling of information by specific applications.
Next generation firewalls (NGFW)
This type is a combination of the other types with additional security software and devices arranged in. Each type has its own strengths and weaknesses, some protect networks at different layers of the OSI model. The benefit of a NGFW is that it combines the strengths of each type cover each type's weakness. An NGFW is often a parcel of technologies under one name as opposed to a single component.
Modern network perimeters have so many entry points and unlike types of users that stronger access control and security at the host are required. This need for a multilayer approach has led to the emergence of NGFWs.
A NGFW integrates three central avails: traditional firewall capabilities, application sensation and an IPS. Similar the introduction of stateful inspection to starting time-generation firewalls, NGFWs bring additional context to the firewall's controlling process.
NGFWs combine the capabilities of traditional enterprise firewalls -- including Network Accost Translation (NAT), Uniform Resource Locator (URL) blocking and virtual individual networks (VPNs) -- with quality of service (QoS) functionality and features non traditionally institute in first-generation products. NGFWs support intent-based networking by including Secure Sockets Layer (SSL) and Secure Beat (SSH) inspection, and reputation-based malware detection. NGFWs also use deep packet inspection (DPI) to check the contents of packets and prevent malware.
When a NGFW, or any firewall is used in conjunction with other devices, it is termed unified threat management (UTM).
Vulnerabilities
Less avant-garde firewalls – package-filtering for instance – are vulnerable to higher-level attacks because they practice not employ DPI to fully examine packets. NGFWs were introduced to address that vulnerability. Still, NGFWs still face challenges and are vulnerable to evolving threats. For this reason, organizations should pair them with other security components, like intrusion detection systems and intrusion prevention systems. Some examples of modern threats that a firewall may exist vulnerable to are:
- Insider attacks: Organizations tin can use internal firewalls on top of a perimeter firewall to segment the network and provide internal protection. If an assail is suspected, organizations can audit sensitive using NGFW features. All the audits should measure up to baseline documentation inside the organization that outlines all-time practices for using the organization's network. Some examples of behavior that might bespeak an insider threat include the following:
- transmission of sensitive data in plain text.
- resource access outside of business concern hours.
- sensitive resource access failure by the user.
- third-party users network resource access.
- Distributed deprival of service (DDos) attacks: A DDoS assail is a malicious attempt to disrupt normal traffic of a targeted network by overwhelming the target or its surrounding infrastructure with a flood of traffic. It utilizes multiple compromised estimator systems as sources of set on traffic. Exploited machines can include computers and other networked resources, such equally cyberspace of things (IoT) devices. A DDoS attack is like a traffic jam preventing regular traffic from arriving at its desired destination. The central concern in mitigating a DDoS set on is differentiating between assail and normal traffic. Many times, the traffic in this attack type tin come from seemingly legitimate sources, and requires cantankerous-checking and auditing from several security components.
- Malware: Malware threats are varied, complex, and constantly evolving aslope security technology and the networks it protects. As networks become more than complex and dynamic with the ascent of IoT, it becomes more difficult for firewalls to defend them.
- Patching/Configuration: A poorly configured firewall or a missed update from the vendor can be detrimental to network security. IT admins should exist proactive in maintaining their security components.
Firewall vendors
Enterprises looking to purchase a firewall should be aware of their needs and empathize their network architecture. In that location are many different types, features, and vendors that specialize in those dissimilar types. Here are a few reputable NGFW vendors:
- Palo Alto: extensive coverage but not inexpensive.
- SonicWall: skillful value and has a range of size enterprises information technology tin can work for. SonicWall has solutions for small, medium or large-calibration networks. Its merely downfall is information technology is somewhat lacking in deject features.
- Cisco: largest breadth of features for an NGFW just not cheap either.
- Sophos: good for midsize enterprises and easy to use.
- Barracuda: decent value, great management, support and cloud features.
- Fortinet: extensive coverage, great value and some deject features.
Time to come of network security
In the early days of the internet, when AT&T's Steven Grand. Bellovin first used the firewall metaphor, network traffic primarily flowed northward-s. This simply means that about of the traffic in a information center flowed from customer to server and server to client. In the by few years, however, virtualization and trends such as converged infrastructure have created more than east-west traffic, which ways that, sometimes, the largest book of traffic in a data centre is moving from server to server. To bargain with this change, some enterprise organizations have migrated from the traditional three-layer data eye architectures to various forms of leaf-spine architectures. This change in architecture has acquired some security experts to warn that, while firewalls yet accept an of import office to play in keeping a network secure, they risk becoming less effective. Some experts even predict a departure from the client server model altogether.
1 potential solution is the use of software-divers perimeters (SDP). An SDP is more than aptly suited to virtual and cloud-based architectures considering it has less latency than a firewall. Information technology also works better within increasingly identity-axial security models. This is considering it focuses on securing user access rather than IP accost-based admission. An SDP is based on a zero-trust framework.
Source: https://www.techtarget.com/searchsecurity/definition/firewall
0 Response to "The Basic Strategy of Log File Reading Is to Determine What Traffic Is Usual. True False"
Post a Comment